Reports sourced from chatter on Twitter reveal that India’s nuclear power infrastructure is being targeted by as-yet unknown cyber intruders. It is now known that the Kudankulam Nuclear Power Plant (KKNPP) in Tamil Nadu was a victim of cyber intrusion.
On 28th October, a handle associated with the network security community brought the matter to light by tagging Brian Bartholomew, a prominent researcher at Kaspersky Lab.
Interesting potential DTRACK (CC @Mao_Ware )
Dumps the data mined output via manually mapped share over SMB to RFC1918 address with a statically encoded user/pass:
> net use \\\\10.38.1.35\\C$ su.controller5kk /user:KKNPP\\administrator
— く̱͕̘͚ず̡̭̠ (@a_tweeter_user) 28 October 2019
The incident was acknowledged by Pukhraj Singh on the same day, who termed the intrusion into KKNPP as Domain Controller-level access through which targeted “extremely mission-critical targets“. For those who may not know, Domain Controllers (DCs) are servers on Microsoft Windows or Windows NT which authenticate security requests and allow access to Windows domain resources.
So, it’s public now. Domain controller-level access at Kudankulam Nuclear Power Plant. The government was notified way back. Extremely mission-critical targets were hit. https://t.co/rFaTeOsZrw pic.twitter.com/OMVvMwizSi
— Pukhraj Singh (@RungRage) 28 October 2019
Singh claimed he was notified about this breach by a third party and promptly informed India’s National Cyber Security Coordinator Lt Gen (Retired) Rajesh Pant on 3rd September for necessary damage control. Furthermore, he revealed that Kaspersky Lab linked these signatures to a Remote Access Trojan (RAT) called DTrack.
I didn’t discover the intrusion, a 3rd party did. It contacted me & I notified National Cyber Security Coordinator on Sep 4 (date is crucial). The 3rd party then shared the IoCs with the NCSC’s office over the proceeding days. Kaspersky reported it later, called it DTrack. https://t.co/9xi4CZrvd1
— Pukhraj Singh (@RungRage) 29 October 2019
Seeing KKNPP’s press release, I would like to add that I notified Lt Gen Rajesh Pant (National Cyber Security Coordinator) on Sep 4. Follow-up emails were exchanged, acknowledging the issue. I would solicit no further enquiries on the matter, requesting privacy. https://t.co/SMdABbJcvQ
— Pukhraj Singh (@RungRage) 29 October 2019
Correction: I notified them on Sep 3. https://t.co/Ww9a3RZTLz
— Pukhraj Singh (@RungRage) 29 October 2019
While sections of the Indian media have been vociferously trying to rebuff claims around the incident, including an official denial by KKNPP, senior government officials acknowledged that a foreign-origin breach had indeed taken place. Reportedly, a cyber audit team was constituted by the National Cyber Security Coordinator comprising technical experts from the Indian Computer Emergency Response Team (CERT-In), National Critical Information Infrastructure Protection Centre (NCIIPC), Ministry of Information & Broadcasting and Department of Telecommunications (Ministry of Communications) to evaluate the veracity of claims. After positive confirmation, an advisory was accordingly shared with KKNPP personnel.
Kaspersky Lab had been following a new Remote Access Trojan (RAT) called Dtrack which was targeting Indian financial institutions since late 2018. The firm believes that its malware attributes have similarities to the exploits used by the infamous Lazarus Group against South Korea; in short, they believe Dtrack may have North Korean origins. Kaspersky researchers believe that presently, Lazarus Group is one of the most active APT groups.
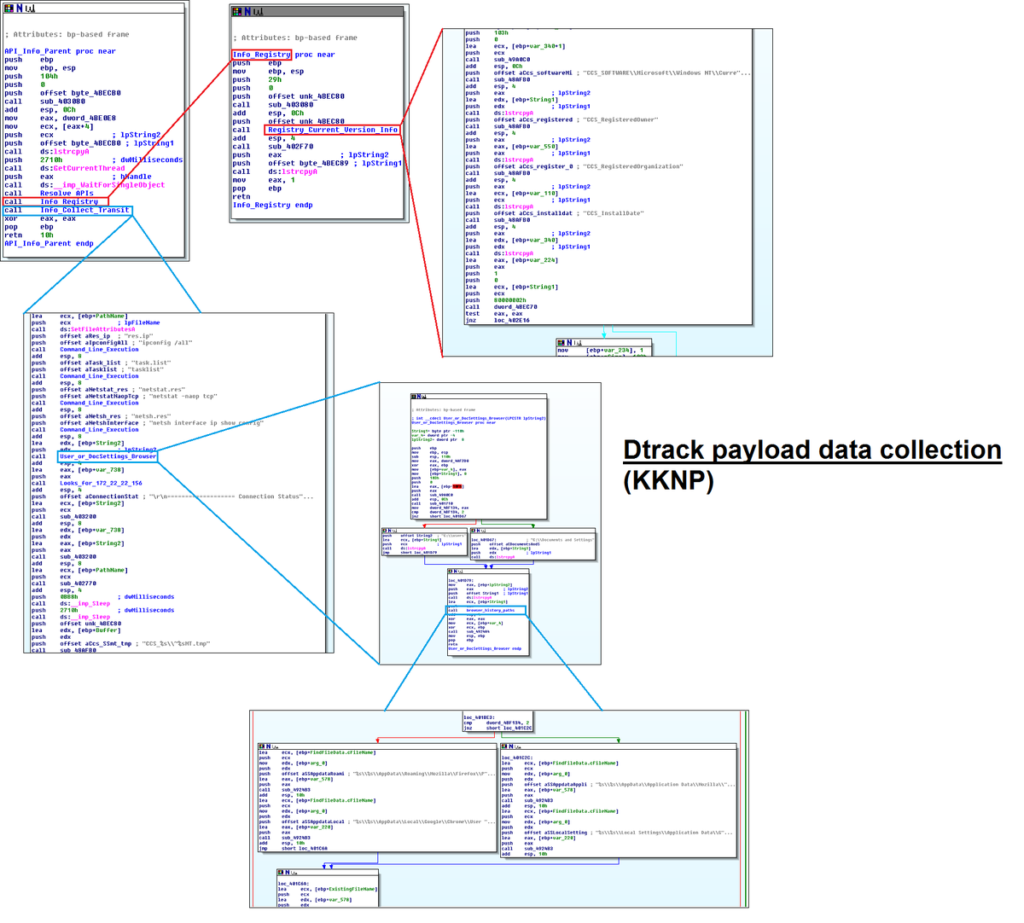
Data from KKNPP which Dtrack was able to exfiltrate include Local IP, MAC IDs, Operating Systems installation/registries, browser history, connectivity to local IPs, compspec, ipconfig and netstat info.
In restrospect, it’s worth highlighting that units at KKNPP have been facing issues since the past few months. In April, Secretary of the Department of Atomic Energy Kamlesh Nilkanth Vyas had acknowledged unusual outages at KKNPP. A report by social volunteer group Poovulagin Nanbargal had reported that Unit 1 of KKNPP had tripped 40 times since 2013 and requested the government to inspect both Units 1 and 2 for detailed evaluation. Since March 2016 alone, Unit-1 tripped 11 times whereas Unit-2 tripped 19 times. Dr M Srinivasan, a former Director at Bhabha Atomic Research Centre, dubbed these frequent outages a “matter of concern“.
Recently on 19th October, Unit-2 stopped generating power, purportedly because of low Steam Generator (SG) level.
While it is unwise to link these frequent unusual outages and dysfunctionalities to cyber intrusions, the possibility of sabotage cannot be ruled out altogether. As the famous example of Stuxnet proves, physically-enabled remote cyber sabotage of nuclear sites is very much possible.
Commenting further on the possibility of Lazarus Group’s i.e. North Korea’s involvement in these intrusions, Singh describes it as “a ridiculously escalatory proliferation/espionage op“.
If it’s N. Korea then this is a ridiculously escalatory proliferation/espionage op. But false flags are so goddamn easy. Kaspersky may be tracking overlapping infra, not this exact campaign. Hack of 2nd target could be power projection. Time lost in IR, we may never really know https://t.co/9xi4CZrvd1
— Pukhraj Singh (@RungRage) 29 October 2019
What’s concerning is that Singh suggests another (more significant) target was also subjected to foreign-origin intrusions.
Actually, the other target scared the shit out of me. Scarier than KKNPP in some ways. So, I went all hyperbolic about casus belli and stuff back then. https://t.co/9xi4CZrvd1
— Pukhraj Singh (@RungRage) 28 October 2019
What could that ‘other (second) target’ be, considered even more significant than KKNPP? Speculations can be many, but as mentioned in his previous tweet, Singh believes that other target was likely kept on sight for “power projection” purposes.
Comments by Pukhraj Singh carry substantial weight. As a qualified Information Security practitioner, he served as Scientist ‘C’ equivalent to Deputy Director at India’s leading technical intelligence agency, the National Technical Research Organisation (NTRO) during the premiership of Manmohan Singh.
His LinkedIn profile claims he was responsible not only for routine cyber defence-related issues but also “geopolitical doctrine formulation” (reportedly approved by then Prime Minister Manmohan Singh) and had experience liaising with NCIIPC, among others. Later on, for more than three years until March 2019, he was Director of Cyber Threat Intelligence at Bhujang Innovations led by Vice Admiral (Retired) DSP Varma who was head of India’s nuclear submarine programme. This impressive portfolio gives unmatched credibility to his claims.
An IAEA publication titled “Computer Security at Nuclear Facilities” (Nuclear Security Series Number 17) lays out guidelines for member states (which include India and Pakistan) on how to establish a computer security programme at a nuclear/radiological facility.
Section 5.9 emphatically points to minimum safeguards through periodic checks against the introduction of vulnerabilities or malware, advising relevant technical experts to evaluate patch management activities so that any technical loopholes can be identified on time.
The cyber intrusion at KKNPP and purported targeting of another more significant entity (indicated by Singh) raise serious concerns around the cyber security of nuclear infrastructure in India. There appears to be a lackadaisal approach toward periodic cyber security audits within India’s nuclear establishment and the NCIIPC appears to have been sleeping rather than following up with the Department of Energy for timely reporting of unusual observations.
The crux of the issue is that the Indian government does not seem to be receiving adequate cyber threat intelligence. Imagine for a moment that the “third party” (informant) who tipped authorities about the incident was never there. Would Dtrack have continued expanding onto supervisory control systems without interruption? What if, one day, Lazarus Group demands ransom from KKNPP in exchange for vacating their servers? This hypothetical scenario in itself is alarming.
On the political-economic front, Russia has been providing equipment for KKNPP. The already-tarnished reputation of this nuclear site in lieu of environmental concerns is further eroded by the lack of adequate cyber security and protocols. This incident can also dent Russia’s nuclear integrity, even if minutely.
A matter of such grave security sensitivities warrants that relevant officials in Pakistan raise the issue with authorities at the IAEA. Separate back-channel discussions with nuclear inspection officials in China and Russia should also be considered. At the very least, IAEA should be urged to send a fact-finding team of technical security experts to India to evaluate vulnerabilities at KKNPP and further scrutinise the functional process through which cyber security audits are conducted.
The BJP government should investigate likelihood of any ‘insider moles‘ who may have enabled remote access to KKNPP, similar to ground assets used by US and Israel against Iran for the successful execution of Stuxnet.
For all its pomp and show including cyber security agreements with major world powers, the ‘effectiveness‘ of India’s nuclear cyber security arrangements has been laid bare.
Pakistan cannot, and should not, ignore the indication of another more important Indian strategic target being similarly compromised. It’s time New Delhi is asked to “do more“.








No comments!
There are no comments yet, but you can be first to comment this article.